Why Insider Risk Management is Critical for Businesses in 2024
In March of 2019, a large auto manufacturer with state-of-the-art, proprietary operations and technology filed a lawsuit against four former employees and a competitor for corporate espionage. The lawsuit was filed after discovering that the employees had downloaded proprietary warehouse schematics and operational procedures before leaving the company and shared them with the competitor.
Trusting employees is key to fostering a dynamic and productive workplace. But with trust also comes risk. Companies need to be able to quickly identify and manage risk from insiders (employees or contractors with corporate access) to minimize the negative impact to their business. Insider threats and risks from illegal, inappropriate, unauthorized, or unethical behavior and actions are a major issue for all companies and can easily go undetected until it is too late. A survey by Crowd Research Partners in 2018 indicated that 90% of organizations feel vulnerable to insider risks and 53% confirmed insider risks against their organization in the previous 12 months. According to a Carnegie Mellon CERT study, 92% of insider threat cases were preceded by a negative work event, such as a termination, demotion, or dispute with a supervisor. And in 2016, Deloitte reported that 59% of employees who leave an organization voluntarily or involuntarily say they take sensitive data with them and that 51% of employees involved in an insider threat incident had a history of violating IT security policies leading up to the incident.
Data breaches are a constant worry for businesses of all sizes. We hear about hackers and cyberattacks all the time, but there’s another, often-overlooked threat lurking inside your organization: insider threats.
The Scope of the Insider Threat Problem
Here are some eye-opening statistics to highlight the seriousness of insider threats:
- Ponemon Institute’s 2023 Cost of a Data Breach Report: Insider threats were the cause of 24% of data breaches in 2023, resulting in an average cost per breach of $5.07 million (https://www.ponemon.org/)
- IBM X-Force Insider Threat Report 2022: 85% of organizations reported experiencing at least one insider threat incident in the past year. (https://www.ibm.com/downloads/cas/ADLMYLAZ)
- Verizon 2023 Data Breach Investigations Report: Privileged misuse (when an insider uses their authorized access for malicious purposes) was the most common insider threat tactic, accounting for 80% of insider breaches. (https://www.verizon.com/business/resources/reports/dbir/)
These statistics paint a clear picture: insider threats are a significant risk, and they’re becoming more common. So, what can businesses do to protect themselves?Insider risk management is a proactive approach that goes beyond simply identifying suspicious individuals. It focuses on:
- Data Security: Protecting sensitive data is paramount. Insider risk management involves monitoring user activity and data access patterns to detect risky behaviors before they escalate into a breach.
- Understanding Intent: Unlike traditional methods that focus solely on malicious intent, insider risk management acknowledges that even unintentional mistakes by employees can lead to data breaches. It implements controls and training to address both scenarios.
- Proactive Approach: Early detection is key. Insider risk management utilizes data analytics and user behavior monitoring to identify potential risks before they escalate into major incidents.
Building a Robust Insider Risk Management Program
Here are some key steps to take:
- Data Classification: Classify your data based on its sensitivity. This helps prioritize risks and implement appropriate security controls.
- User Access Controls: Implement the principle of least privilege, granting users only the access level they need to perform their jobs.
- Data Activity Monitoring: Monitor user activity related to sensitive data access and flag suspicious patterns for investigation.
- Security Awareness Training: Educate employees on data security best practices and how to identify and report suspicious activity.
- Incident Response Plan: Develop a plan for responding to insider threat incidents quickly and effectively.
Microsoft Purview: A Multifaceted Approach to Insider Risk
Microsoft Purview goes beyond basic security by providing functionalities specifically designed to address insider threats. Here’s how it helps:
- Data Loss Prevention (DLP): Purview DLP helps you identify, classify, and protect sensitive data across your organization’s Microsoft 365 environment. By setting DLP policies, you can prevent unauthorized data exfiltration attempts, whether intentional or accidental.
- Insider Risk Management: This dedicated Purview solution leverages machine learning and user behavior analytics to identify potential insider risks. It analyzes various signals, including data access patterns, email activity, and downloaded files, to detect anomalies that might indicate malicious intent or risky behavior.
- User Activity Monitoring: Gain granular visibility into user activities across Microsoft 365 applications. Purview allows you to monitor user access attempts, downloads, and file modifications, enabling you to identify suspicious activities and investigate potential insider threats.
- Advanced Analytics: Purview provides powerful analytics capabilities that help you correlate data from various sources to build a comprehensive picture of user behavior and identify potential risks. This proactive approach allows you to intervene before a security breach occurs.
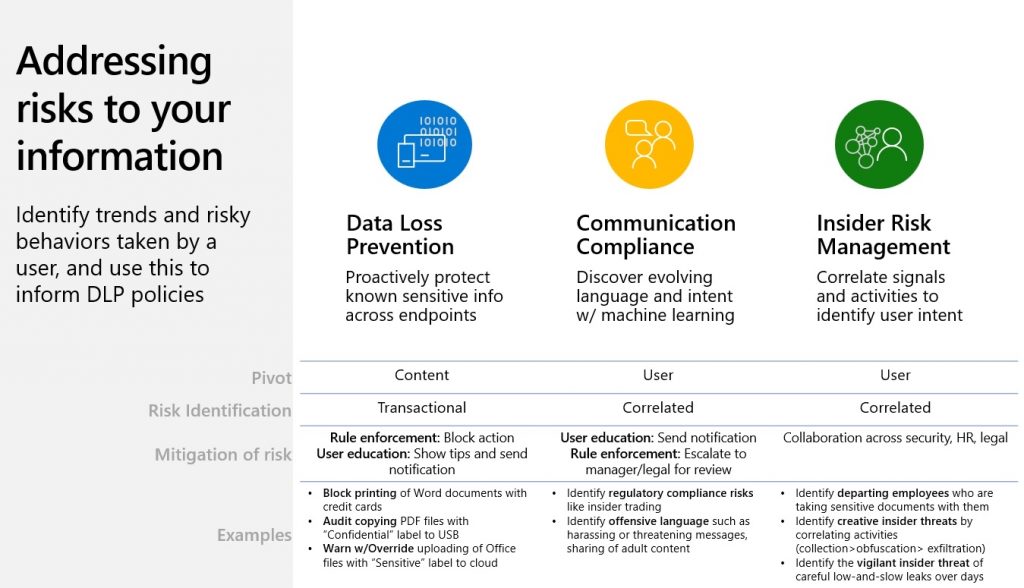
Benefits of Using Microsoft Purview for Insider Risk Management:
- Reduced Risk of Data Breaches: By proactively identifying and addressing potential insider threats, Purview helps minimize the risk of data breaches and protects your sensitive information.
- Improved Security Posture: Purview strengthens your organization’s overall security posture by providing a multi-layered approach to insider risk mitigation.
- Enhanced Compliance: Purview helps you comply with data privacy regulations by ensuring the secure handling of sensitive information.
- Simplified Investigations: Purview facilitates efficient investigations by providing centralized access to user activity data and insights into potential insider threats.
Taking Action Against Insider Threats
Microsoft Purview empowers organizations to move beyond reactive security measures and implement a proactive insider risk management strategy. By leveraging its comprehensive set of tools and functionalities, you can gain valuable insights into user behavior, identify potential risks, and take timely action to safeguard your sensitive data.
By implementing a comprehensive insider risk management program, organizations can significantly reduce their risk of data breaches caused by insiders. This proactive approach can save businesses millions of dollars, protect their reputation, and ensure the security of their sensitive data.
Remember, insider risk management is an ongoing process. Regularly review and update your program to stay ahead of evolving threats.
